We recently ran a one-day workshop on web security for technologists at the Government Digital Service (GDS). Security is a topic where lots of people lack confidence in their skills so we thought it was a valuable area to focus on. This was our first time running a workshop so we described it as an alpha and used the opportunity to assess how web security could best be taught.
Some developers at GDS have been on security courses in the past but we thought we could run something to better meet our organisation’s needs, even though we aren’t security experts.
We had some hypotheses on what areas we should cover in the workshop. For example, we felt we could cover the Open Web Application Security Project (OWASP) Top 10 in a single day. We thought that doing practical exercises in the languages and frameworks people use on a daily basis would highlight common security pitfalls for people to be aware of. We also thought that discussing examples of real application vulnerabilities we’ve found and fixed in the past would help people understand the security field more.
Who we invited
The technology community at GDS is quite big so we limited the people we invited to those who currently work on GOV.UK rather than all project teams. The exception we made is that we invited all the junior technologists at GDS because of the workshop’s importance to learning and development.
We had participants with skills ranging from frontend and backend development to web operations so they could contribute their varied expertise to the group. Most of the developers who attended use Ruby on Rails in their work, which let us focus our practical exercises on that framework.
What topics we covered
Although we wanted to cover the OWASP Top 10, we felt that running through all the points in order wasn’t going to be the most useful way of structuring the day. Many categories in the list overlap with each other and some vulnerabilities can be explained quickly while others are much more complex to understand.
Instead we spent the morning focusing on things that happen on the server, like structured query language (SQL) injections, and the afternoon on things that happen on browsers, like cross-site scripting and cross-site request forgery.
For each vulnerability we discussed the theory behind it and then did some practical exercises. Some exercises involved exploiting the vulnerabilities to better understand how they work. For this we used RailsGoat, a deliberately vulnerable Rails application designed for educating developers about security.
We also discussed examples of times where we’ve inadvertently introduced vulnerabilities through our day-to-day work on GOV.UK. We wanted to bring home to people how easy it is to overlook security considerations, even when you understand them.
It’s impossible for a service to never have a security problem, but increasing our understanding of web security will improve how we react and respond to issues when we need to (James Stewart detailed this in a blog post on holistic security recently).
Bob Walker, who leads our Web Operations community, joined us halfway through the day to explain how internet technologies work, like transport-layer security. He gave a demo of tcpdump on a local network to show how easy it is for plaintext HTTP requests to be intercepted while they travel across the internet.
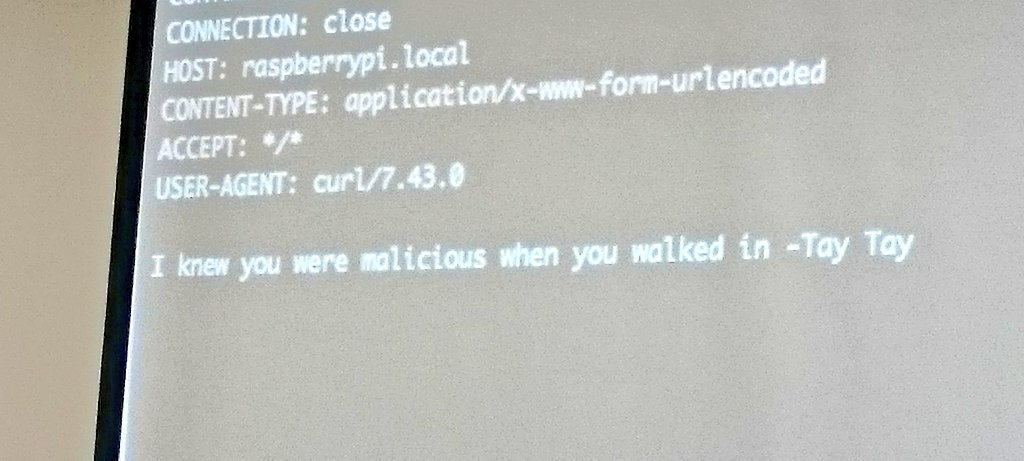
Jenny wrote a small Python app that receives HTTP requests and logs them to disk files on a Raspberry Pi when connected to a local network. We were able to display the most recent requests on a projector screen (shown below) so that people could experiment with cross-site scripting and see how attackers can retrieve sensitive information from their victims.
Our end of day retrospective
We ran a retrospective at the end of the day and had lots of positive feedback. People found the practical exercises very useful for consolidating topics they knew about only in theory. They also felt that discussing real examples of vulnerabilities on familiar systems was an effective way of learning about security. Many people enjoyed learning more about networking - this is a potential topic for a future workshop.
We had lots of fun organising the day, and we learnt a lot too as we were reminding ourselves of the details of vulnerabilities and trying to figure out all the things you need to do to mitigate them.
Learnings for next time
We could have spent more time preparing what we wanted to talk about on the day; not as much as for a conference talk (which should be one hour for every minute you’re on stage), but still more than we did.
Several people said that it would have been helpful if we’d given more structure around the practical exercises. And we should have done a bit more to encourage communication throughout the day, for example we could have set up a Slack channel, had more frequent breaks, and been better about moving people around so that they got to work in different pairs.
We’d like to get some training on running workshops - perhaps from the delivery management community, who are probably the people at GDS most practiced in organising large groups of people.
Several people who couldn’t come said that they would love to attend this workshop in the future. Other people at GDS will probably run it next time but we’ll help them by sharing all our notes, Trello board and slides.
There is a big appetite for these kind of tech workshop sessions, so it’d be great if people from different parts of GDS (or even across government) organised similar sessions on other topics.
Please let us know if you’re already planning anything by leaving a comment in the section below.
You can follow Alex and Jenny on Twitter, sign up now for email updates from this blog or subscribe to the feed.
If this sounds like a good place to work, take a look at Working for GDS - we're usually in search of talented people to come and join the team.